Saving six round trips with OCSP stapling
Local Developer Discovers One Weird Trick To Shave Seconds Off Page Load Time!
I was trying to figure out why my site was so slow on my phone after I enabled HTTPS. After all, TLS is supposed to be fast now, right? But even when there was plenty of bandwidth, it still took several seconds to load a page of text.
One WebPageTest later, and I found the problem. Check out items 2 through 5 (yikes):
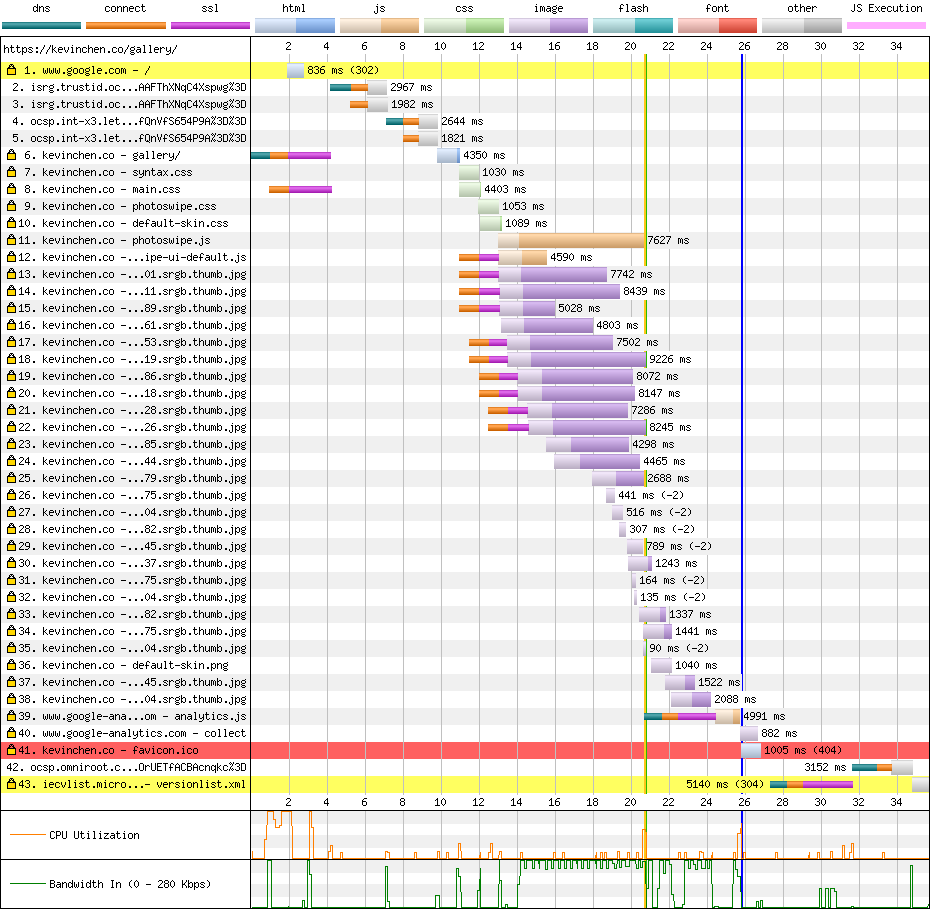
Why does the browser spend time on ocsp.identrust.com and
ocsp.int-x3.letsencrypt.org? They’re definitely not domains the user
requested.
Revoking certificates
Let’s say a hacker gains root on your web server and steals your private keys. Even if you generate a new key and the Certificate Authority issues a new certificate, what’s stopping the attacker from impersonating your site until the old certificate expires?
These days, when a browser receives a certificate from a server, it asks the CA whether the certificate has been revoked. The protocol is called OCSP, and it’s really expensive for browsers. According to the waterfall chart above, the browser made a DNS query, a TCP connection, and an OCSP request — for each certificate in the chain!
My website’s chain contains two certificates after the root, so a browser using OCSP makes six additional round trips! If my round trip time is 300 ms in spotty coverage, OCSP checks will take nearly two seconds to complete.
To make matters worse, many browsers block requesting or rendering the page’s contents until they hear that a certificate is valid. So, while I thought my phone was busy fetching the contents of the page, it actually spent most of its time verifying certificates.
Enter OCSP stapling
OCSP stapling works around this problem. It moves the burden of making OCSP requests to the server, where resources are cheaper. The server attaches the CA’s signed OCSP response to the certificate. Since the responses expire after some time, the browser knows that the certificate it received hasn’t been revoked recently.
I followed SSLMate’s tutorial to enable OCSP stapling on this site. Now, it loads a whole 6 seconds faster in the worst-case scenario!